engineer analysis on rfid chip The UHF RFID system-level link budget, the key technique in RFID such as SJC, and the key RF performance requirement were then analyzed. Lastly, an ADF9010- and . $9.99
0 · RFID Tag Analysis Using an Equivalent Circuit
1 · RFID Device Security Testing
2 · RFID Chips 101
3 · RFID Chips
4 · Numerical Modeling, Analysis, and Optimization of RFID Tags
5 · Enhancing supply chain performance using RFID technology and
6 · Developing a UHF RFID Reader RF Front End with an Analog
7 · Design, analysis, and realisation of chipless RFID tag for
8 · Analysis and Study on RFID Tag Failure Phenomenon
9 · (PDF) RFID Applications and Security Review
Fast, updating NFL football game scores and stats as games are in progress are provided by CBSSports.com. Sports Watch . NFC Wild Card Playoff, Lumen Field, Seattle, WA. Recap;
The UHF RFID system-level link budget, the key technique in RFID such as SJC, and the key RF performance requirement were then analyzed. Lastly, an ADF9010- and .
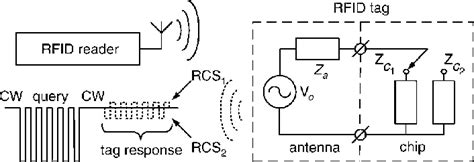
We apply our general analysis to a 70 mm x 14 mm T-matched RFID tag with Monza R6 and show a good agreement between the model, the measurements, and the derived formulas. I. .
Exponent’s computer scientists and electrical engineers can help secure radio frequency identification (RFID)-equipped security devices like credit cards, IDs, smart cards, and access . RFID (radio frequency identification) tags play a crucial role in a wide range of applications, from wireless communications to personal tracking and smart city infrastructure. Discover the power of RFID chips — integrated circuits revolutionizing tracking and security solutions. We discuss RFID chip frequencies, architecture, capabilities, and more. This paper presents a review of the most cited topics regarding RFID focused on applications, security, and privacy.
RFID Tag Analysis Using an Equivalent Circuit
The Xerafy engineering team’s guide to RFID chips used in asset tracking and inventory management. Passive UHF RFID chips compliant with EPCglobal Gen2v2 and ISO 18000-63 .
In this study, prototypes of two distinct 8-bit chipless RFID tags operating in 3–6 GHz utilising L-resonators discussed in Section 2 are reported. The chipless tags have been . RFID helps to digitize supply chains as the technology generates automated sensor data that can be further analyzed for automation and optimization. RFID technology functions .
RFID tag’s failure analysis, which is a specialized area with long history and evolved with advances in science and technology, has apparently made a big contribution to delivering . The UHF RFID system-level link budget, the key technique in RFID such as SJC, and the key RF performance requirement were then analyzed. Lastly, an ADF9010- and AD9963-based solution, as well as an AD9361-based UHF RFID reader RF front end, are set up to test system-level performance.
RFID Device Security Testing
We apply our general analysis to a 70 mm x 14 mm T-matched RFID tag with Monza R6 and show a good agreement between the model, the measurements, and the derived formulas. I. INTRODUCTION RFID is a technology with a long history, and UHF RFID (also known as RAIN RFID) is a major part of it.
Exponent’s computer scientists and electrical engineers can help secure radio frequency identification (RFID)-equipped security devices like credit cards, IDs, smart cards, and access badges against malicious attacks. RFID (radio frequency identification) tags play a crucial role in a wide range of applications, from wireless communications to personal tracking and smart city infrastructure. Discover the power of RFID chips — integrated circuits revolutionizing tracking and security solutions. We discuss RFID chip frequencies, architecture, capabilities, and more. This paper presents a review of the most cited topics regarding RFID focused on applications, security, and privacy.
RFID Chips 101
The Xerafy engineering team’s guide to RFID chips used in asset tracking and inventory management. Passive UHF RFID chips compliant with EPCglobal Gen2v2 and ISO 18000-63 standards have found widespread application in various industrial settings, facilitating reliable asset tracking and inventory management systems. In this study, prototypes of two distinct 8-bit chipless RFID tags operating in 3–6 GHz utilising L-resonators discussed in Section 2 are reported. The chipless tags have been designed using CST Microwave Design Studio and printed on the Roger RT 5880 substrate.
RFID helps to digitize supply chains as the technology generates automated sensor data that can be further analyzed for automation and optimization. RFID technology functions by identifying the presence of an object, recording the data, and storing that information (Musa et . RFID tag’s failure analysis, which is a specialized area with long history and evolved with advances in science and technology, has apparently made a big contribution to delivering mutually beneficial output in both physics-of-failure and reliability tests.
The UHF RFID system-level link budget, the key technique in RFID such as SJC, and the key RF performance requirement were then analyzed. Lastly, an ADF9010- and AD9963-based solution, as well as an AD9361-based UHF RFID reader RF front end, are set up to test system-level performance.
We apply our general analysis to a 70 mm x 14 mm T-matched RFID tag with Monza R6 and show a good agreement between the model, the measurements, and the derived formulas. I. INTRODUCTION RFID is a technology with a long history, and UHF RFID (also known as RAIN RFID) is a major part of it.Exponent’s computer scientists and electrical engineers can help secure radio frequency identification (RFID)-equipped security devices like credit cards, IDs, smart cards, and access badges against malicious attacks. RFID (radio frequency identification) tags play a crucial role in a wide range of applications, from wireless communications to personal tracking and smart city infrastructure. Discover the power of RFID chips — integrated circuits revolutionizing tracking and security solutions. We discuss RFID chip frequencies, architecture, capabilities, and more.
This paper presents a review of the most cited topics regarding RFID focused on applications, security, and privacy.The Xerafy engineering team’s guide to RFID chips used in asset tracking and inventory management. Passive UHF RFID chips compliant with EPCglobal Gen2v2 and ISO 18000-63 standards have found widespread application in various industrial settings, facilitating reliable asset tracking and inventory management systems. In this study, prototypes of two distinct 8-bit chipless RFID tags operating in 3–6 GHz utilising L-resonators discussed in Section 2 are reported. The chipless tags have been designed using CST Microwave Design Studio and printed on the Roger RT 5880 substrate. RFID helps to digitize supply chains as the technology generates automated sensor data that can be further analyzed for automation and optimization. RFID technology functions by identifying the presence of an object, recording the data, and storing that information (Musa et .
RFID Chips

Numerical Modeling, Analysis, and Optimization of RFID Tags
Enhancing supply chain performance using RFID technology and
In the divisional round, the Green Bay Packers, Tennessee Titans, 49ers and Chiefs advanced to play in the conference title games. From the wild-card round through .
engineer analysis on rfid chip|(PDF) RFID Applications and Security Review